Backup Bitlocker Keys to Active Directory
Jump to navigation
Jump to search
The following instructions can be used to force a supported Microsoft Windows operating system to backup its encryption key to Active Directory for safe keeping. Please note that if you have setup bitlocker GPOs with existing encrypted devices already in production, you will need to run this command on those existing endpoints.
- Press Windows key to show the start menu & type "cmd" to bring up a search for Windows Command Prompt
- Right click Windows Command Prompt and select "Run as Administrator"
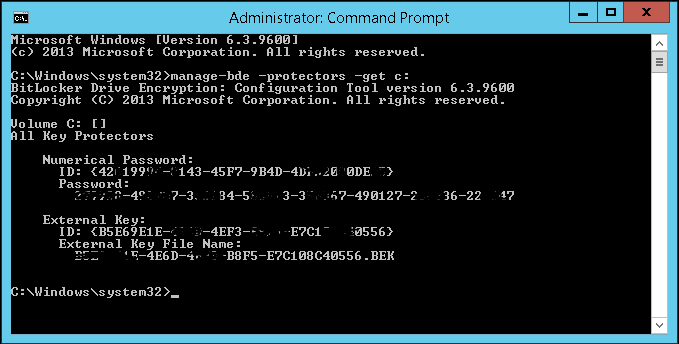
- Enter the following command:
manage-bde -protectors -get c:[1]
- From here you should copy the "Numerical Password ID with the brackets"
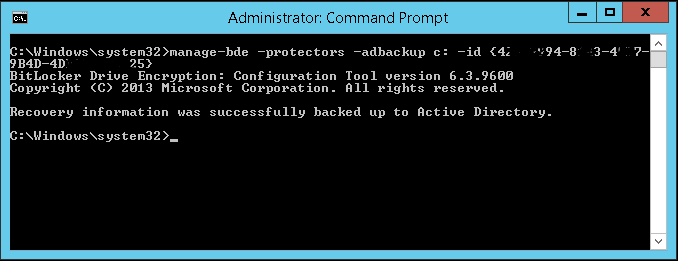
- Enter the following command with numerical ID from above inserted
manage-bde -protectors -adbackup c: -id {yourNumbericalPassword}[1]
- You should see that your key was successfully backed up to Active Directory
References
- ↑ 1.0 1.1 Jack Stromberg, jackstromberg.com, February 4, 2015