Difference between revisions of "Backup Bitlocker Keys to Active Directory"
Jump to navigation
Jump to search
(Added main content and image examples) |
(Added introduction and changed first steps on running cmd as admin) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | + | The following instructions can be used to force a supported Microsoft Windows operating system to backup its encryption key to Active Directory for safe keeping. Please note that if you have setup bitlocker GPOs with existing encrypted devices already in production, you will need to run this command on those existing endpoints. | |
| − | + | *Press Windows key to show the start menu & type "cmd" to bring up a search for Windows Command Prompt | |
| − | + | *Right click Windows Command Prompt and select '''"Run as Administrator"''' | |
| − | ::<code>manage-bde -protectors -get c:</code> | + | *Enter the following command: |
| − | + | ::<code>manage-bde -protectors -get c:</code><ref name="jack" /> | |
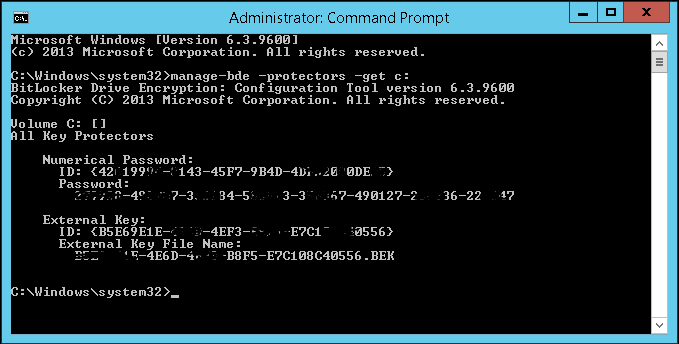
| + | *From here you should copy the "Numerical Password ID with the brackets" | ||
::[[File:Bitlocker AD Protectors.PNG|none|frame|400px|Example of Step 3. Keys have been blurred on purpose]] | ::[[File:Bitlocker AD Protectors.PNG|none|frame|400px|Example of Step 3. Keys have been blurred on purpose]] | ||
| − | + | *Enter the following command with numerical ID from above inserted | |
| − | ::<code>manage-bde -protectors -adbackup c: -id {'''yourNumbericalPassword'''} | + | ::<code>manage-bde -protectors -adbackup c: -id {'''yourNumbericalPassword'''}</code><ref name="jack" /> |
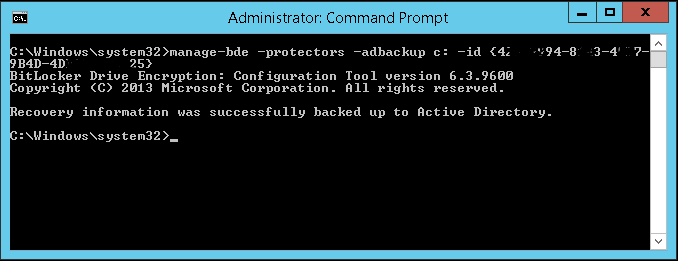
| − | + | *You should see that your key was successfully backed up to Active Directory | |
::[[File:Bitlocker AD Backup Success.PNG|none|frame|400px|Example of Step 6. Key Number has been blurred on purpose]] | ::[[File:Bitlocker AD Backup Success.PNG|none|frame|400px|Example of Step 6. Key Number has been blurred on purpose]] | ||
| + | |||
| + | ==References== | ||
| + | <references> | ||
| + | <ref name="jack">Jack Stromberg, [http://jackstromberg.com jackstromberg.com], February 4, 2015</ref> | ||
| + | </references> | ||
| + | [[Category:Microsoft]] | ||
Latest revision as of 13:27, 1 December 2017
The following instructions can be used to force a supported Microsoft Windows operating system to backup its encryption key to Active Directory for safe keeping. Please note that if you have setup bitlocker GPOs with existing encrypted devices already in production, you will need to run this command on those existing endpoints.
- Press Windows key to show the start menu & type "cmd" to bring up a search for Windows Command Prompt
- Right click Windows Command Prompt and select "Run as Administrator"
- Enter the following command:
manage-bde -protectors -get c:[1]
- From here you should copy the "Numerical Password ID with the brackets"
- Enter the following command with numerical ID from above inserted
manage-bde -protectors -adbackup c: -id {yourNumbericalPassword}[1]
- You should see that your key was successfully backed up to Active Directory
References
- ↑ 1.0 1.1 Jack Stromberg, jackstromberg.com, February 4, 2015